Certain vulnerabilities in Nginx are version-specific, and exposing version numbers may provide attackers with exploitable information. Hiding Nginx version information is a simple yet effective server security measure.
By default, Nginx includes a Server field in response headers containing both the Nginx name and version information. The default 4xx/5xx error pages also display the Nginx version number.
Checking if Nginx version information is hidden
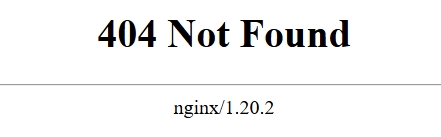
Access a non-existent page through your browser and check whether the returned 404 page contains version information:
Alternatively, use HTTP request tools to inspect server response headers. The following example uses the curl command in Linux:
curl -I http://127.0.0.1
HTTP/1.1 200 OK Server: nginx/1.20.2 Date: Wed, 09 Jul 2025 10:44:01 GMT Content-Type: text/html; charset=utf-8 Transfer-Encoding: chunked Connection: keep-alive
The Server field value nginx/1.20.2 contains the version information.
Hiding version information
Edit the Nginx configuration file nginx.conf and add the following directive within the http block:
server_tokens off;
Restart the Nginx service for the changes to take effect.
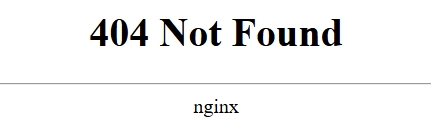
To restore version information display, simply remove this directive or change the parameter to on.